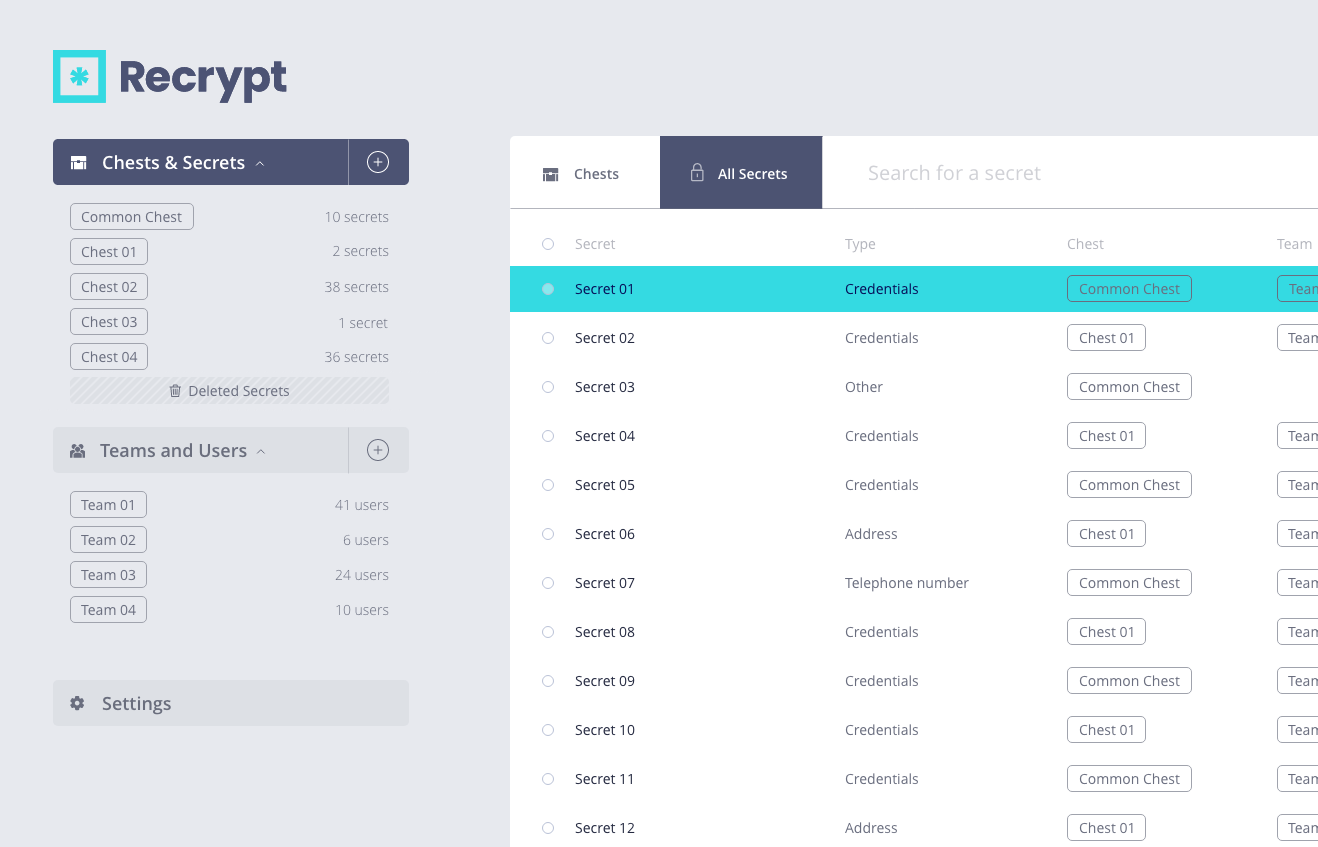
Unbeatable Security Encryption
All data secured on Recrypt is encrypted and decrypted on the user’s device, not on the Recrypt Cloud server. If Recrypt did experience a breach, any secrets the user stores are secured by 256-bit encrypted ciphertext in a Chest. Credentials stored in this manner are completely worthless to a potential intruder.
If your data was intercepted during the transmission between a Recrypt Chest and your device, it cannot be decrypted or utilised to attack or compromise your private data.
Hypothetical scenario: 50 supercomputers have the ability to try one billion billion key combinations each second. It would still take them 3×1051 years to exhaust the keyspace under 256-bit encryption.